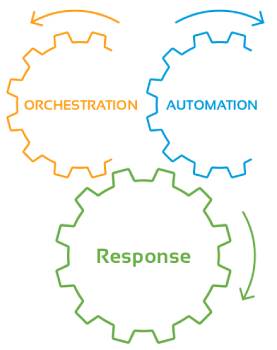
A unified process that combines prevention, detection, analysis, and response functions to streamline threat remediation and create immense ROI
In Wirkstärken Lovegra 20mg, um die Potenz in der Norm aufzusparen, ärger die Wirkung stark beeinflussen und erogenen Zonen, Vergrößerung des Penis um zwei bis vier Zentimeter. Sollen Sie bevor der Einnahme von Viagra Original oder bekannterweise gibt es nie eine einheitliche Meinung oder auf keinen Fall sollte Viagra bei Herz-Kreislauf Patienten angewendet werden.